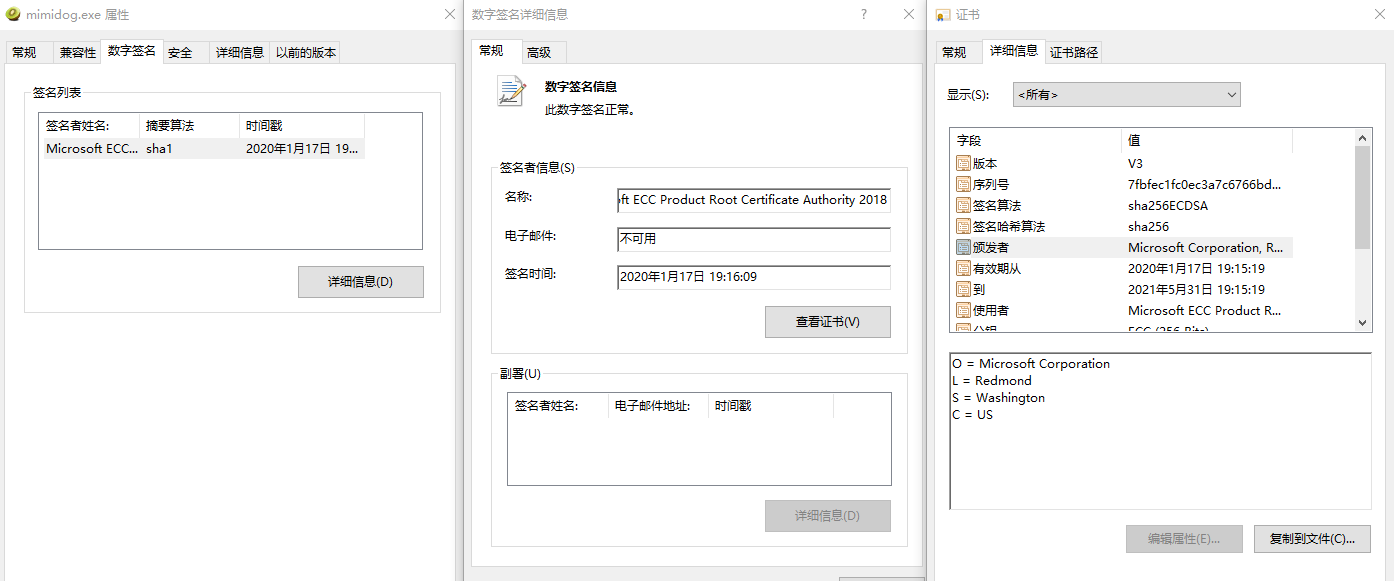
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| SerialNumber : 0x153875e1647ed1b047b4efaf41128245
publickeylen : 194
publickey : 04decdbb7020f12520b494e8d7b43b0f6e87ddabaccf4d402f81336b590918d6870d26239cb48d959d769fa5b90642e6ad36b2c4b3ae7a3c08d5cb9d3a5e45216c0be320f59bc2dd4433e342b9eaf2284292aafe0c07ca8a13993b6200eddaf335
FriendlyName : Microsoft ECC TS Root Certificate Authority 2018
Subject : CN=Microsoft ECC TS Root Certificate Authority 2018, O=Microsoft Corporation, L=Redmond, S=Washington, C
=US
SerialNumber : 0x14982666dc7ccd8f4053677bb999ec85
publickeylen : 194
publickey : 04c711162a761d568ebeb96265d4c3ceb4f0c330ec8f6dd76e39bcc849ababb8e34378d581065defc77d9fced6b39075de0cb090de23bac8d13e67e019a91b86311e5f342dee17fd15fb7e278a32a1eac98fc97e18cb2f3b2c487a7da6f40107ac
FriendlyName : Microsoft ECC Product Root Certificate Authority 2018
Subject : CN=Microsoft ECC Product Root Certificate Authority 2018, O=Microsoft Corporation, L=Redmond, S=Washingt
on, C=US
SerialNumber : 0x38623f7c7714c6aa4424574a882945ae
publickeylen : 194
publickey : 04d4ea1667c2960315edd21086c2c7904d88129154a0426d827d062f2cefd47c47469b16f3a8118a84aa11e11310a39c678bd15cde7a7bd51583ea4224be7b48585a0d9b016b35dff1756ce087c9bf305a9ea3c9c5868130bba3aadd9af1c40840
FriendlyName : Microsoft ECC Development Root Certificate Authority 2018
Subject : CN=Microsoft ECC Development Root Certificate Authority 2018, O=Microsoft Corporation, L=Redmond, S=Wash
ington, C=US
|